Although all 10 of the ISC2 domains are related to computer security not all of the. Your apps are not restricted by the DNS settings for your App Service Environments default domain suffix to only be accessible by those domain names.
A Basic Guide On Cyber Security For Beginners 2022 Edition Simplilearn
Confidential Secret and Top Secret are three security domains used by the US.

. More often than not operations sees the application and associated requirements on the eve of deployment. Study with Quizlet and memorize flashcards terms like What are the 3 security domains Which of these things is part of the CYBER domain What are some non-technical physical steps you can take to being a great human firewall. Security and Risk Management.
More broadly defined domains are groups of subjects and objects with similar security requirements. Physical People and Cyber. ISC² defines and organizes the CISSP domains based on its survey of the cybersecurity industry often referred to as a job task study JTA.
A key element of building an effective human firewall is to make employees care about cybersecurity. A security domain is considered to be an application or collection of applications that all trust a common. Custom domain suffix is an internal load balancer ILB App Service Environment feature that allows you to use your own domain suffix to access the apps in your App Service Environment.
What are cybersecurity domains. A5 Information security policies. Make People Care about Cybersecurity.
Of the 3 fundamentals to cybersecurity security and risk management deals with the people and processesSecurity and risk management ensures the security threats and risks are at an acceptable level. Application and Systems Development Security. The CISSP CBK domains are updated every three years to keep up ensure professionals are tested on the latest topic areas relevant to the roles and.
A security domain is the list of objects a subject is allowed to access. Security categories and control objectives. The Compliance Council details the Security Domains as below.
The three primary tenets for information security governance and risk management are. What are 3 security domains. What are the three security domains quizlet.
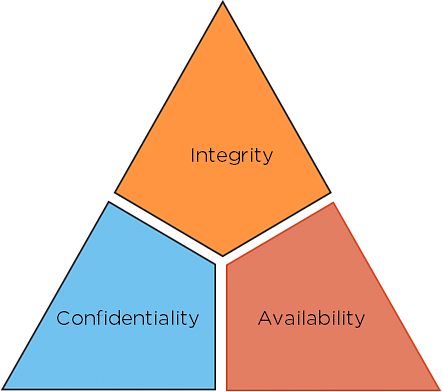
What are 3 key ingredients for an excellent human firewall. The three goals of security are confidentiality integrity and availability. Security and risk management is one of the largest domains in cybersecurity.
What are the two most common causes of. A51 Management direction for. Confidential Secret and Top Secret are three security domains used by.
What are the 3 security domains. The CIA Triad below outlines these three tenets. A network with a different security domain is kept separate from other networks.
Knowledge sharing is the process of transferring tacit undocumented and explicit documented information from one person to another. In this article we take a look at the 14 security domains specific to ISO 27001. Common sense street smarts and situational security awareness.
Ongoing training related to security threats and best practices to avoid falling for these threats. To me application security can be neatly divided into three key domains. Which of these things is part of the CYBER domain.
A domain that implements a security policy and is administered by a single authority. Confidential Secret and Top Secret are three security domains used by the US. A security domain is the list of objects a subject is allowed to access.
What are the three ingredients for an excellent human firewall. Confidentiality integrity and availability CIA. Architecture Secure Coding and Testing.
Security may not see the design at all but will rather be expected to pull out a tool for testing also on the eve of. A security domain is the determining factor in the classification of an enclave of serverscomputers. A security domain is the list of objects a subject is allowed to access.
The security architecture domain refer to a plan and set of principles that describe the security services that a system is required to provide to meet the needs of its users the system elements. For example NIPRNet SIPRNet JWICS and NSANet are all kept separate. Department of Defense DoD for example.
It focuses on the understanding and alertness of employees and how they can make smarter security decisions. In an organization sharing knowledge not only increases productivity but it also empowers employees to do their jobs effectively and efficiently. More broadly defined domains are groups of subjects and objects with similar security requirements.
Department of Defense DoD for example. An environment or context that includes a set of system resources and a set of system entities that have the right to access the resources as defined by a common security policy security model or security architecture. A brief overview of the eight CISSP domains.

Security Domain An Overview Sciencedirect Topics

Domain Isolation Policy Design Windows Windows Security Microsoft Docs

The Chief Information Security Officer Ciso Role Explained Bmc Software Blogs

Pdf Importance Of Cyber Security And Its Sub Domains

Information Security Unit Ppt Download

3 Security Domain Classification Download Scientific Diagram
Baseline Security Requirements For Network Security Zones Version 2 0 Itsp 80 022 Canadian Centre For Cyber Security

Cissp Common Body Of Knowledge Review Information Security Risk Management Domain Version Ppt Download
0 comments
Post a Comment